A tutorial on configuring SSH Server to Authenticate with Private/Public Keys using Ubuntu Linux. 2/5 in a series on SSH and key pair authentication http://www.danscourses.com/Linux-Fundamentals. Ssh(1) obtains configuration data from the following sources in the following order: 1. Command-line options 2. User's configuration file (/.ssh/config) 3. System-wide configuration file (/etc/ssh/sshconfig) For each parameter, the first obtained.
ON THIS PAGE
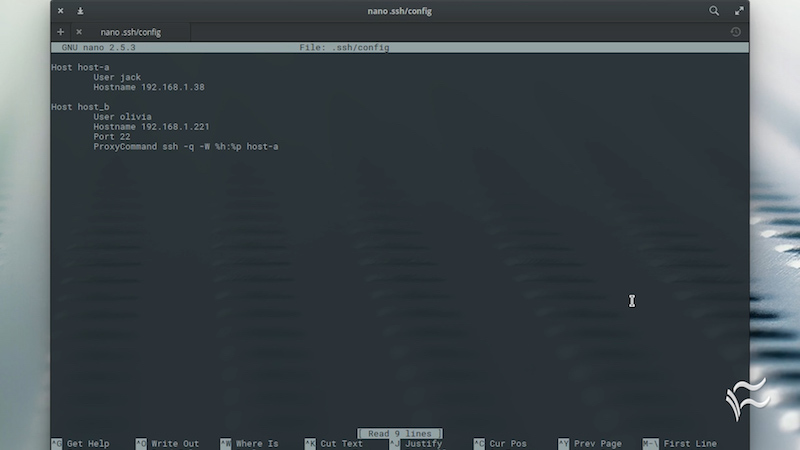
Make SSH easy by adding entries to your local SSH config file. From this file we can set useful defaults to make logging into remote servers as easy as `ssh myserver`.
When the router, switch, or security deviceis powered on first time, it is ready to be configured. Initially,you log in as the user root with no password. Later, youmust configure a plain-text password for the root-level user (whoseusername is root). Configuring a plain-text passwordis one way to protect access to the root level by unauthorized users.If you forget the root password for the router, you can use the passwordrecovery procedure to reset the root password. Read this topic formore information.
Configuring the Root Password
The Junos OS is preinstalled on the router or switch.When the router or switch is powered on, it is ready to be configured.Initially, you log in as the user root with no password.The root directory of a UNIX device is the entry point to all otherfolders and files on that device. As a result, access to the rootdirectory is restricted by default to a predefined user account knownas the root user. The root user (also referredto as superuser) has unrestricted access andfull permissions within the system. The expression “log in asroot” is commonly used when an action requires the user to loginto the device as the root user.
If you configure a blank password using the encrypted-password statement at the [edit system root-authentication] hierarchylevel for root authentication, you can commit a configuration butyou cannot log in as the root user and gain rootlevel access to the router or switch.
After you log in, you should configure the root (superuser)password by including the root-authentication statementat the [edit system] hierarchy level and configuring oneof the password options:
Ssh Config Set Password Mac
MYPASSENVVAR=SomePassword MYPASSWDFROMFILE=$ (. Ssh/config git remote set-url origin git@github.
If you configure the plain-text-password option, you are prompted to enter and confirm the password:
The default requirements for plain-text passwordsare:
The password must be between 6 and 128 characters long
You can include most character classes in a password (uppercaseletters, lowercase letters, numbers, punctuation marks, and otherspecial characters). Control characters are not recommended.
Valid passwords must contain at least one uppercase letteror one lowercase letter, or one character class.
You canuse the load-key-file URL filename statement to load an SSH key file that was previously generatedusing ssh-keygen. The URL filename is the path to the file’s location and name. When using thisoption, the contents of the key file are copied into the configurationimmediately after entering the load-key-fileURL statement. This command loads RSA (SSH version 1 andSSH version 2) and DSA (SSH version 2) public keys.
Starting in Junos OSRelease 18.3R1, the ssh-dss and ssh-dsa hostkeyalgorithms are deprecated— rather than immediately removed—toprovide backward compatibility and a chance to bring your configurationinto compliance with the new configuration.
Optionally, you can use the ssh-dsa, ssh-ecdsa, or ssh-rsa statements to directly configureSSH RSA, DSA, or ECDSA keys to authenticate root logins. You can configuremore than one public key for SSH authentication of root logins aswell as for user accounts. When a user logs in as root, the publickeys are referenced to determine whether the private key matches anyof them.
From configuration mode, you can confirm yourSSH key entries by entering the show command. It shouldlook something like this:
Junos-FIPSsoftware has special password requirements. FIPS passwords must bebetween 10 and 20 characters in length. Passwords must use at leastthree of the five defined character sets (uppercase letters, lowercaseletters, digits, punctuation marks, and other special characters).If Junos-FIPS is installed on the router or switch, you cannot configurepasswords unless they meet this standard.
If you use the encrypted-password option, then anull-password (empty) is not permitted. You must configure a passwordwhose number of characters range from 1 through 128 characters andenclose the password in quotation marks.
See Also
Example: Configuring a Plain-Text Password for Root Logins
This example shows how to configure a plain-textpassword for the root-level user (whose username is root). Configuring a plain-text password is one way to protect accessto the root level by unauthorized users. You must prevent unauthorizedusers from gaining access to superuser commands that can be used toalter your system configuration.

Requirements
No special configuration beyond device initializationis required before configuring this example.

Make sure that you understand the requirements for avalid plain-text password. For Junos OS, the default requirementsfor a plain-text password are as follows:
Must be from 6 up to 128 characters long.
Can include most character classes (uppercase letters,lowercase letters, numbers, punctuation marks, and other special characters).Control characters are not recommended.
Must contain at least one change of case or characterclass.
Overview
Junos OS is preinstalled on the router. When the router is poweredon, it is ready to be configured. Initially, you log in as the root-leveluser with no password. To set the root password, you have severaloptions. This example shows how to enter a plain-text password thatJunos OS then encrypts for you.
Configuration
CLI Quick Configuration
To quickly configure this example, copy thefollowing command and paste it into the window. When prompted, typethe new password, and then when prompted, retype it.
Configuring a Plain-Text Password for User Root
Step-by-Step Procedure
To configure a plain-text password for the root-leveluser:
Type the
setcommand for the plain-text passwordand press Enter.Type the new password next to the
New passwordprompt and press Enter.Retype the same password next to the
Retype new passwordprompt and press Enter.
Results
From configuration mode, confirm your configurationby using the show command. It should look something likethis:
If the output does not display the intended configuration, repeatthe instructions in this example to correct the configuration.
After you have confirmed that the configuration is correct,enter commit from configuration mode.
Verification
Verifying the Configuration of a Plain-Text Password for UserRoot
Purpose
Verify the configuration of a plain-text password forthe root-level user.
Action
From operational mode, confirm your configuration byentering the show configuration system command.
Meaning
If you use a clear-text password, Junos OS displaysthe password as an encrypted string so that users viewing the configurationcannot see the unencrypted password. That is, as you enter the passwordin plain text, Junos OS encrypts it immediately. You do not have toconfigure Junos OS to encrypt the password as in some other systems.Plain-text passwords are hidden and marked as ## SECRET-DATA in theconfiguration.
Ssh Config File
See Also
Example: Configuring SSH Authentication for Root Logins
The following example shows how to configure two publicDSA keys for SSH authentication of root logins:
Related Documentation
Openssh Config Password
